Security is an evergreen concern businesses of all types and volumes face. To address it, substantial investments are made regularly. AI, in turn, can help address this request with even more to offer.
In this piece, we will examine how custom AI solutions can increase and improve your business's security. We’ll overview AI's role in security, see what challenges it can solve, and consider the benefits it can bring.
Understanding business security challenges
Nowadays, there’s a vast array of security threats that can compromise, disrupt, and damage businesses, affecting their sensitive data. Before implementing AI to solve specific security issues, you need to acknowledge all of the known issues and any potential ones.
- Cyberattacks. These encompass various forms of attacks including phishing, DDoS attacks, malware, and more. With these tactics, criminals gain access to a company’s internal networks and steal data or hold systems hostage.
- Insider threats. Your protective efforts should also be aimed at the internal side of the business, as employees and their accesses can pose significant security risks. Insider threats can result from deliberate sabotage, accidental data leaks, or inadequate security practices.
- Data breaches. Unauthorized access to personal data, like customer details or intellectual property, can cause all sorts of problems, from legal consequences to financial losses, and poor reputation.
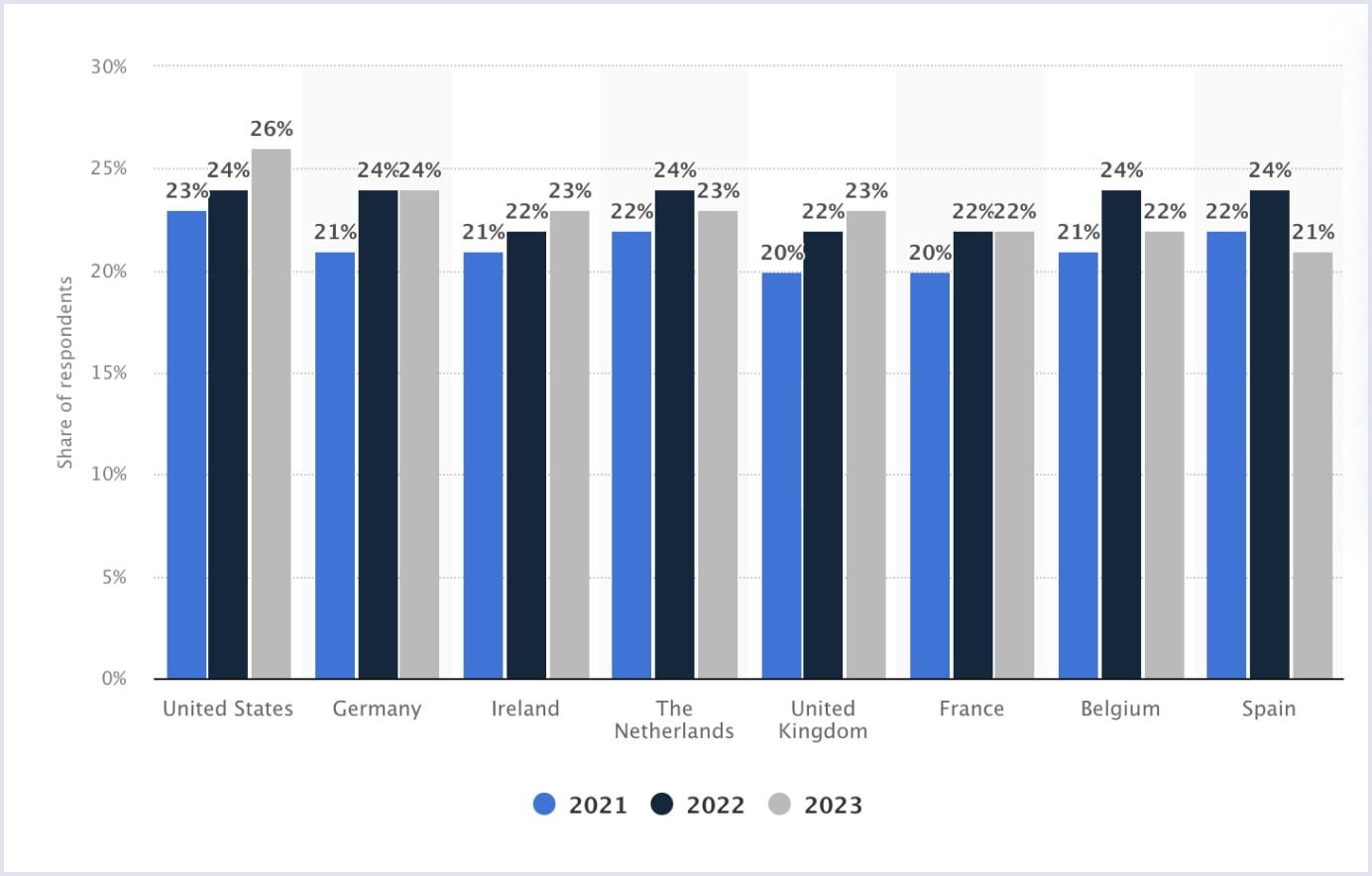
With all the security challenges businesses face, proactive security practices are essentially the best way to deal with threats. Instead of only addressing issues after they take place, you must take a preventative approach to security. Besides, the statistical data only supports the statement. Businesses throughout Europe and the US spend up to 26% of their funds on security, which, in fact, is a huge number.
Unfortunately, the majority of traditional security solutions like firewalls, antivirus software, and surveillance systems can rarely provide space for proactivity. Despite a foundational level of protection, these solutions have limitations and are less performant in quickly growing cyberspace.
For this reason, AI gets implemented, as it is trained to not only detect issues but also help prevent them in the future. So, let’s see how AI tools can boost your security.
The role of AI in improving security
First of all, artificial intelligence in security essentially means implementing AI computational powers, algorithms, and machine learning techniques to deal with security threats. In this regard, AI is particularly helpful as it works with vast arrays of data over short periods of time. After all, in security, it relies on several key technologies:
- Machine learning. ML algorithms use data analysis to see certain patterns and predict future potential threats. Besides, ML systems learn from the data they receive, improving their accuracy over time.
- Natural language processing. With NLP, your AI system can read and comprehend human language. In security, this ability is super helpful in analyzing everything where the human factor is involved, namely communication channels and open information sources. These, for instance, include spam, phishing attempts, or suspicious links analysis for signs of malicious intent.
- Behavioral analytics. Using AI, you can analyze user behavior on your platform to detect anomalies that might indicate a security threat. For example, if an employee suddenly begins accessing files they’ve never touched before, an AI system could flag this as suspicious and trigger an investigation.

Key applications of AI in business security
Fraud detection
Traditional fraud detection methods are designed to work according to predefined rules, which can be avoided using more complex tactics. AI, in turn, employs its data analyzing capabilities of transactional and behavioral data in real time, identifying anomalies in their early stage. With various algorithms, AI systems can:
- Identify unusual patterns. There are many deviations from normal behavior AI can detect. They often include unexpectedly large transactions, various login locations, or abnormal purchase patterns, which could be involved in fraudulent activities.
- Enhance accuracy. AI models can be fed with historical fraud data, letting them see even the smallest indicators of fraud that may be missed by traditional methods. Consequently, as these models study new data, they become even more accurate over time.
- Automate decision-making. AI systems can automatically flag or block suspicious transactions, reducing the time and effort required by human analysts to identify and respond to potential fraud.
- Reduce false positives. By analyzing multiple data points and using advanced algorithms, AI can minimize the number of false positives, ensuring that legitimate transactions are not unnecessarily interrupted.
Read also: AI for Startups: Use Cases and Role in Early-Stage Success
Threat intelligence
Basically, threat intelligence is all about collecting, processing, and taking measures on information about potential or actual threats to an organization. Therefore, in threat intelligence, AI can do several things.
For starters, it can aggregate threat data from social media and security feeds to deliver a comprehensive overview of the threat situation as a whole. Next, AI can use the aggregated data to predict potential dangers before they materialize. This, in turn, makes the previously mentioned proactive measures possible.
Secondly, AI-powered threat intelligence platforms can not only analyze but also provide context to identified threats, ultimately helping security teams prioritize responses based on the severity and relevance of the threat to their specific environment.
Access control
Another aspect AI can enhance is the access control. It is a critical aspect of business security, which is responsible for letting only authorized individuals to access certain data. Hence, if you’re seeking to improve internal access control, here’s how AI can assist.
- Biometric authentication. You can teach AI-powered security solutions to read biometric data. As a result, it can require facial or voice recognition to verify identities within a company with high accuracy. These systems are more difficult to bypass than traditional password-based methods.
- Adaptive access control. Artificial intelligence can regulate access permissions employees have based on various contextual factors that’s programmed in it. For example, if an employee attempts to access a secure system from an unusual location or outside of normal working hours, the AI system may require additional authentication or temporarily restrict access.
- Anomaly detection. AI can monitor access patterns and automatically identify anomalies indicating that something has gone wrong. For instance, if an employee suddenly accesses files or systems outside their usual scope of work, the AI system can flag this behavior for further investigation.
- Policy enforcement. AI can help enforce access control policies more effectively by ensuring that permissions are consistently applied across all systems and adjusting them as needed based on changes in employee roles or organizational structure.
Custom AI solutions vs. off-the-shelf security products
Custom AI solutions we build at Codica are designed to meet the unique security requirements of a specific business, providing a level of precision and adaptability that off-the-shelf products often cannot match. Therefore, our AI development services and custom AI-based security system development in particular, offer several substantial benefits.
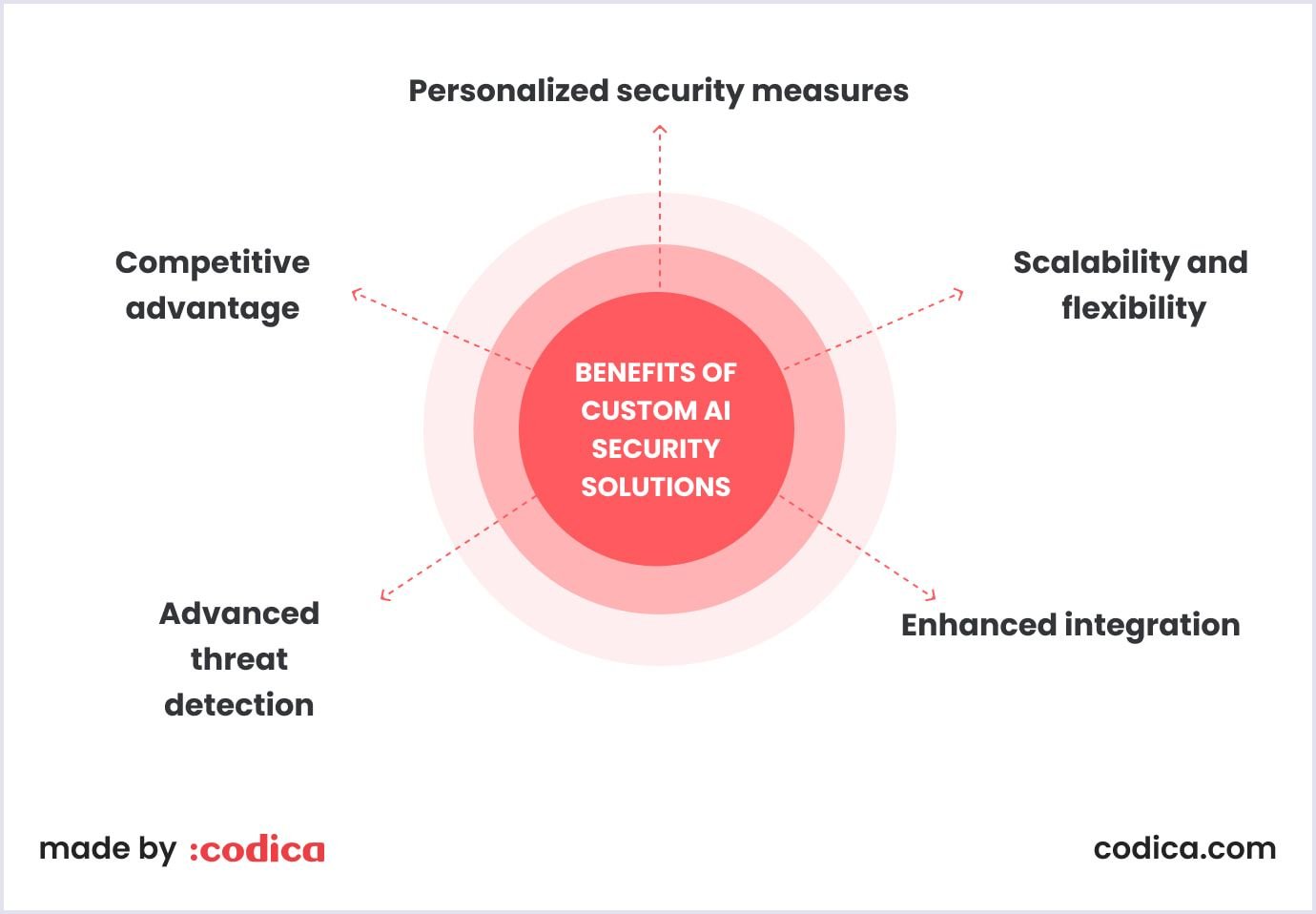
- Personalized security measures. Custom AI solutions we build are developed with a deep understanding of a business’s specific threats, vulnerabilities, and operational environment. This ensures that everything we develop is highly relevant and effective.
- Scalability and flexibility. Custom solutions developed by our professionals can be scaled and adapted as the business grows or its security needs to evolve. Whether it’s integrating new types of data, expanding into different markets, or addressing new threats, custom AI can be adjusted to fit changing requirements.
- Enhanced integration. Custom AI systems can be seamlessly integrated with a business’s existing infrastructure, ensuring that all components work harmoniously. This will help you negate some compatibility issues and make the overall operation swifter.
- Advanced threat detection. By taking advantage of AI models trained on specific data relevant to your niche, our products can detect nuanced and sophisticated threats that generic software might miss.
- Competitive advantage. Businesses using custom AI solutions can gain a competitive edge by having a security system that not only protects assets but also optimizes operations and reduces risk more effectively than standardized solutions.
Steps to implement custom AI security solutions
Assessing security needs
The first step in implementing custom AI security solutions is to thoroughly assess the specific security needs of your business. First and foremost, you need to understand what you want to protect your business against. This can be both threats you already have experience dealing with and new ones which you’re afraid of.
However, the evaluation of your needs can be challenging if you’re not sure what solutions are present on the market. For this reason, our product discovery services would be a perfect first step to start the process.
Essentially, product discovery helps with lots of aspects even before the implementation starts. From our perspective, we conduct an in-depth analysis of the problems you face, as well as come up with ideas on how to solve them.
Regarding custom AI implementation, product discovery will help you understand which technologies to choose, what benefits they will bring, and what challenges can come up along the way. From our side, we provide all the essential information on future development, outlining the best tech stack, time, and cost estimates for this implementation, and suggest the best ways to achieve the desired result.
Developing and integrating AI solutions
With all the preparatory steps taken, the development starts with the carte blanche, as both you and your development partner are aligned on the specifications of the project.
After the planning, the development starts. We develop AI models that are specifically trained on data relevant to your business. This often involves working with AI experts and ML specialists to create models that can accurately detect the unique threats you face.
As in any product development, the working build undergoes pilot testing before full-scale deployment. In other words, we employ test-driven development where your AI solution gets to work in a controlled environment, where developers can analyze its performance, fix bugs, and measure product-specific metrics. This allows us, as a development team, to make sure we deliver a robust and 100% working solution.
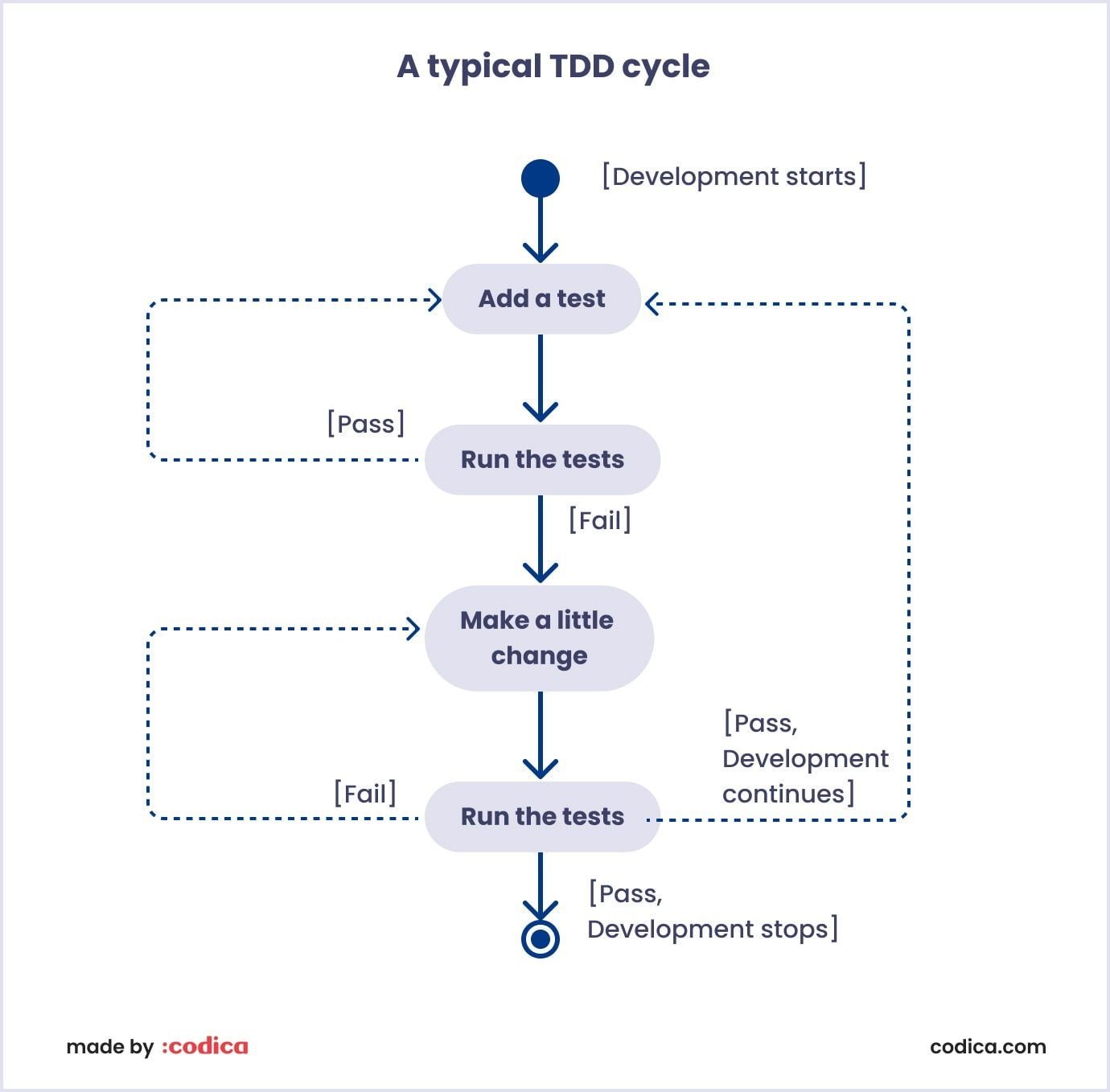
Besides, we are no strangers to iterative development, which we believe should be a must in the AI development process. The point is, custom AI solutions often require ongoing refinement and adjusting. Hence, feedback from previous QA services helps our team to continuously improve the AI models and their performance.

Integration with existing security systems
Custom AI security solutions don’t exist in a vacuum. Instead, they are built to be applicable to existing businesses and team up with existing security measures. Therefore, the successful implementation of a custom AI solution requires seamless integration with your existing security infrastructure. In this process, there are several cornerstones worth noting.
First and foremost, it’s a compatibility assessment. Even before the development, we make sure that the AI solution we develop is compatible with your current security systems.
The second concern is data integration. When implementing a new solution to the well-established infrastructure, we have to make sure it’s possible to Integrate data from existing systems. This allows the newly built AI system to analyze data from multiple sources, enhancing its ability to detect and respond to threats.
Another part of the setup is automation and orchestration we love AI for. The interaction between the AI security system and other solutions should be manually set up. It is needed so that, for instance, when AI detects a threat, it can automatically trigger actions like blocking an IP address or alerting the security team.
Last but not least, AI systems require maintenance. Once integrated, we continuously monitor the AI solution’s performance and its interaction with other systems. Regular maintenance and updates are crucial to make sure that all cogs remain effective and performant.
Conclusion
In summary, custom AI solutions pose more than enough benefits to be considered the new security standard for businesses. They are performant, scalable and are continuously becoming more and more powerful.
Apart from security, AI solutions are capable of improving lots of operations within the business. For this reason, feel free to check out our blog to learn more about AI's influence, benefits, and implementation in various domains. Lastly, if you looking for ways to integrate AI into your operations, be it shopping, support, or security, contact us, so that we can provide the most comprehensive overview of how you can do it.

