Architecture is one of the foundational pillars that define your marketplace’s success in the long run. Creating an efficient marketplace requires an architecture that can handle complex demands with ease, and in this regard, MACH architecture offers a fantastic solution.
Yet, architecture itself rarely impacts security. But this is not the case with MACH. Each component of MACH plays a crucial role in enhancing both security and flexibility.
Together, these principles equip marketplace platforms with the agility to face present and newcoming business needs and challenges.
So, let’s unwrap this security thread and analyze what security challenges you might meet and how MACH can tackle them.
How MACH principles enhance marketplace security
First of all, MACH is about modularity, where all its components (i.e., microservices, API-first, cloud-native, and headless) have their distinct roles and responsibilities. This approach of dividing responsibilities between different elements makes each element more secure as a unit. Let’s take a look at each.
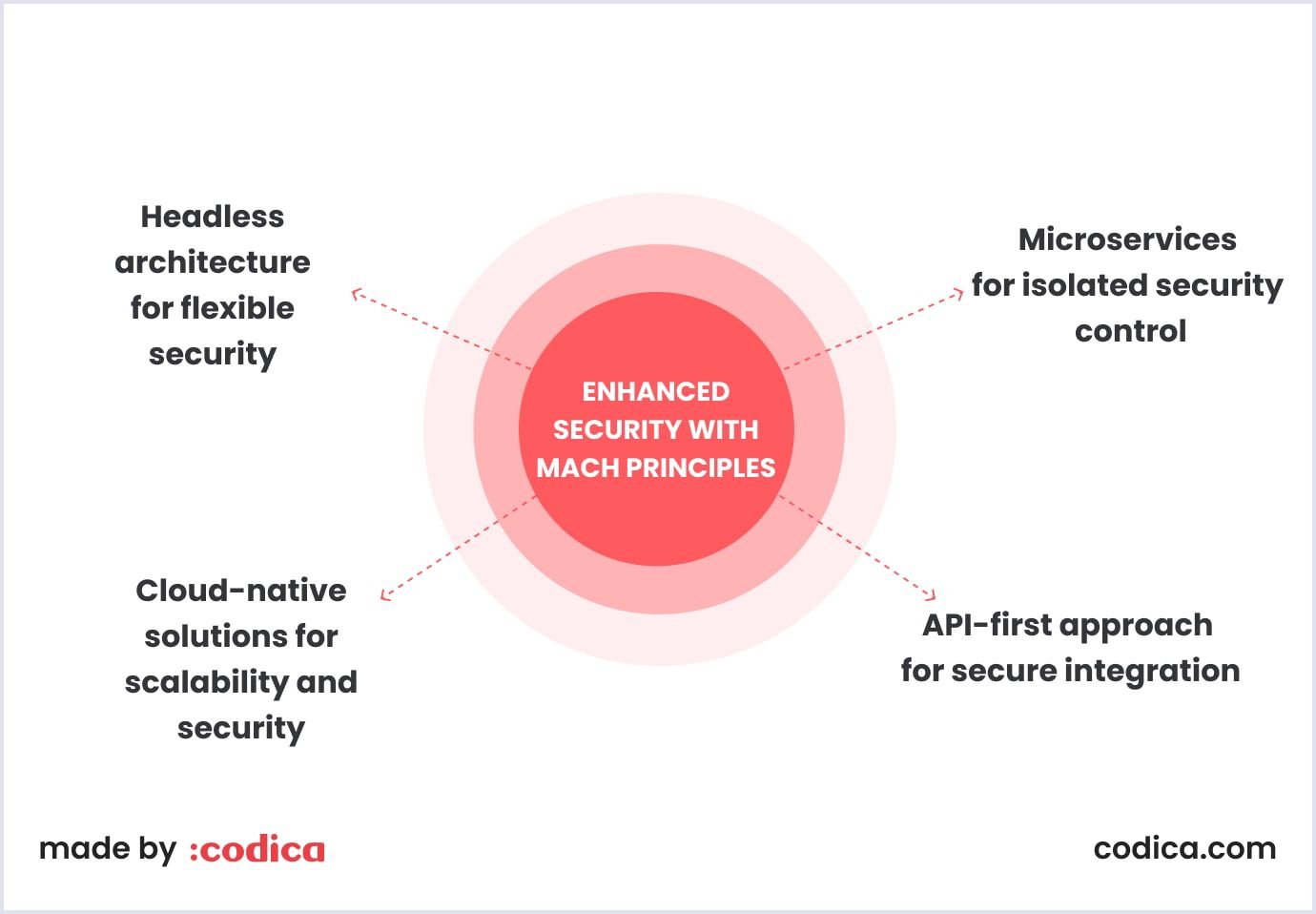
Microservices for isolated security control
First of all, what are microservices? In projects with MACH infrastructure, microservices break down a platform into small, independent services like payments, authentication, and product catalog management.
So what’s the point? This isolation provides a major security advantage:
Each service can have targeted security measures specific to its function.
This setup boosts security: if one service is compromised, others remain protected, limiting the potential impact of an attack.
API-first approach for secure integration
In MACH infrastructure, an API-first approach means that APIs are the primary method for components to interact with each other. This ensures secure, controlled data exchange between services.
With this approach, developers can design APIs with security in mind from the beginning, gradually adding various security protocols like OAuth and MFA authentication, tokenization, TLS encryption and others.
APIs provide a controlled interface for services to interact, ensuring that only approved entities can access or modify data.
In the aftermath, secure API-first architecture prevents unauthorized access and protects data, creating a safe communication environment across the platform.

Cloud-native solutions for scalability and security
Cloud-native solutions are perfect for security. Why? Because they take advantage of built-in cloud features like:
- Encryption;
- Access controls;
- Data redundancy.
All these features ensure data security and scalability. They support robust identity and access management (IAM) for precise user permissions, automatic backups for data protection, and resilience to scale securely while handling increased demand or attacks.
Headless architecture for flexible security
Essentially, headless architecture separates frontend (user interface) from the backend (data and processing).
Why is it beneficial for security? With this setup, you can develop security measures specifically for each part.
For example, you can secure front-end interfaces with authentication and backend with data encryption and access control. Here’s how headless architecture security works in a nutshell, particularly in MACH architecture:
This flexible security model is ideal for marketplaces that support multiple front-end interfaces, like web, mobile, and IoT applications. It ensures that each channel has security measures tailored to its unique risks and requirements.
Best practices for securing marketplaces with MACH principles
MACH implementation opens many opportunities to enhance security. Here are some best practices to protect marketplace operators and users from security threats.
Implement robust data encryption
Data encryption protects sensitive marketplace data in two states: when it is stored and when it is moving across networks. Thus, there are two opposing types of encryption you can utilize:
- Encryption at rest. Protects data stored on devices or servers (e.g., files on a disk, databases). It makes sure that all the data is safe without the decryption key in case the storage is compromised.
- Encryption in transit. It safeguards your data when it moves between microservices or in user-server communication. With protocols like Transport Layer Security (TLS), data is less likely to be intercepted when it moves between points.
In addition to these two, there are other encryption methods. You can use end-to-end encryption, which is a highly popular technology that ensures only the intended recipient can decrypt the data they receive.
Lastly, there’s tokenization. While not traditional encryption, it replaces sensitive data with tokens, which adds a layer of security for stored data. However, it’s technically different from encryption because it doesn’t use a reversible key-based process.

Use OAuth and multi-factor authentication
Next up in our list of practices are OAuth and MFA. Let’s see what they can do for your marketplace.
OAuth is a protocol that allows third-party applications to access marketplace resources without needing to reveal or store user credentials. OAuth relies on trusted providers to log users into their accounts.
Simply put, OAuth is that same pop-up window asking whether you want to log in with your Google, Apple, Facebook, or any other trusted account.
OAuth is often combined with MFA, which requires additional identity verification via SMS or biometrics. It makes the marketplace more secure against unauthorized access as only verified users gain access.
Additionally, there are other authentication protocols you can use. Here’s a short list:
- JWT (JSON Web Tokens). A small, secure token that includes user details like ID or roles. Each service can check these tokens without needing a central system.
- OpenID Connect (OIDC). An extension of OAuth 2.0 that adds identity checks and single sign-on (SSO). It uses tokens to confirm who the user is and shares their details with services.
- Token-based authentication. Users get a token after logging in, and this token is sent with every request. Services check the token locally or with a central system.
- Certificate-based authentication. Uses digital certificates to confirm the identities of users or services. Certificates are checked against a trusted list, ensuring secure communication.
- API Keys. Unique codes given to apps or services for identification. Services check these keys against a list to allow or deny access.
In the aftermath, the combination of these protocols makes it practically impossible to hack into users’ accounts.
Monitor and audit microservices continuously
The more your marketplace grows, the more possibilities for a security breach appear. Thus, it’s essential to implement continuous monitoring and auditing to detect unusual activity and prevent potential breaches.
Monitoring tools like Prometheus, Elastic Stack, AWS CloudWatch, and others can track service-to-service communication, detect unauthorized access attempts, and monitor traffic patterns. Logging each transaction allows for detailed forensic analysis if suspicious behavior is detected.
Regular audits also help maintain the security posture of each microservice, enabling rapid identification and response to vulnerabilities.
Regular penetration testing and vulnerability scans
To keep your marketplace environment secure, testing of all kinds must take place. Why?
This approach is proactive, meaning that you’re most likely to identify issues with the platform before someone finds a way to exploit them.
But what are these penetration tests and vulnerability scans? Let’s look at both.
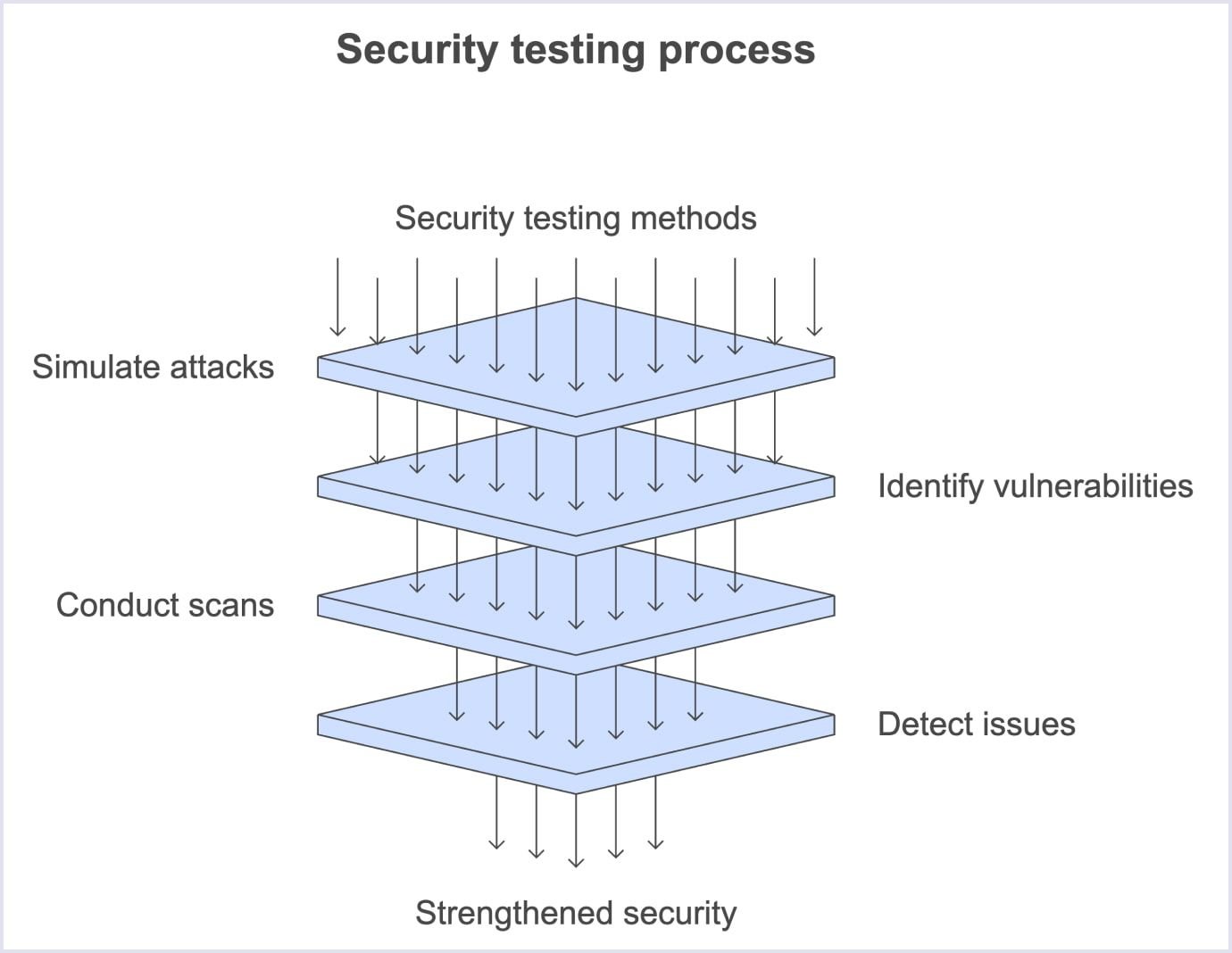
- Penetration testing for marketplaces simulates potential attacks to test the defenses of the marketplace. It is done by QA specialists who replicate various techniques hackers use to uncover potential vulnerabilities. These tests can reveal weaknesses in APIs, network configurations, and authentication mechanisms.
- Vulnerability scans search through the code and infrastructure to find weak spots. Unlike penetration testing, vulnerability scans are quicker and help detect known security issues across large portions of the system. Vulnerability scans look for issues with outdated libraries, poorly managed configurations, or vulnerabilities in third-party dependencies.
Strategies for building a resilient and future-proof security framework
As with any architecture, you will need to develop a thoughtful security framework. In this context, it refers to a structured set of guidelines, practices, and tools designed to protect a marketplace platform from security threats.
You can, for instance, list strategies, technologies, and processes you or your marketplace development partner use to secure data, control access, and monitor for potential vulnerabilities. Here are a few tips from the Codica team.
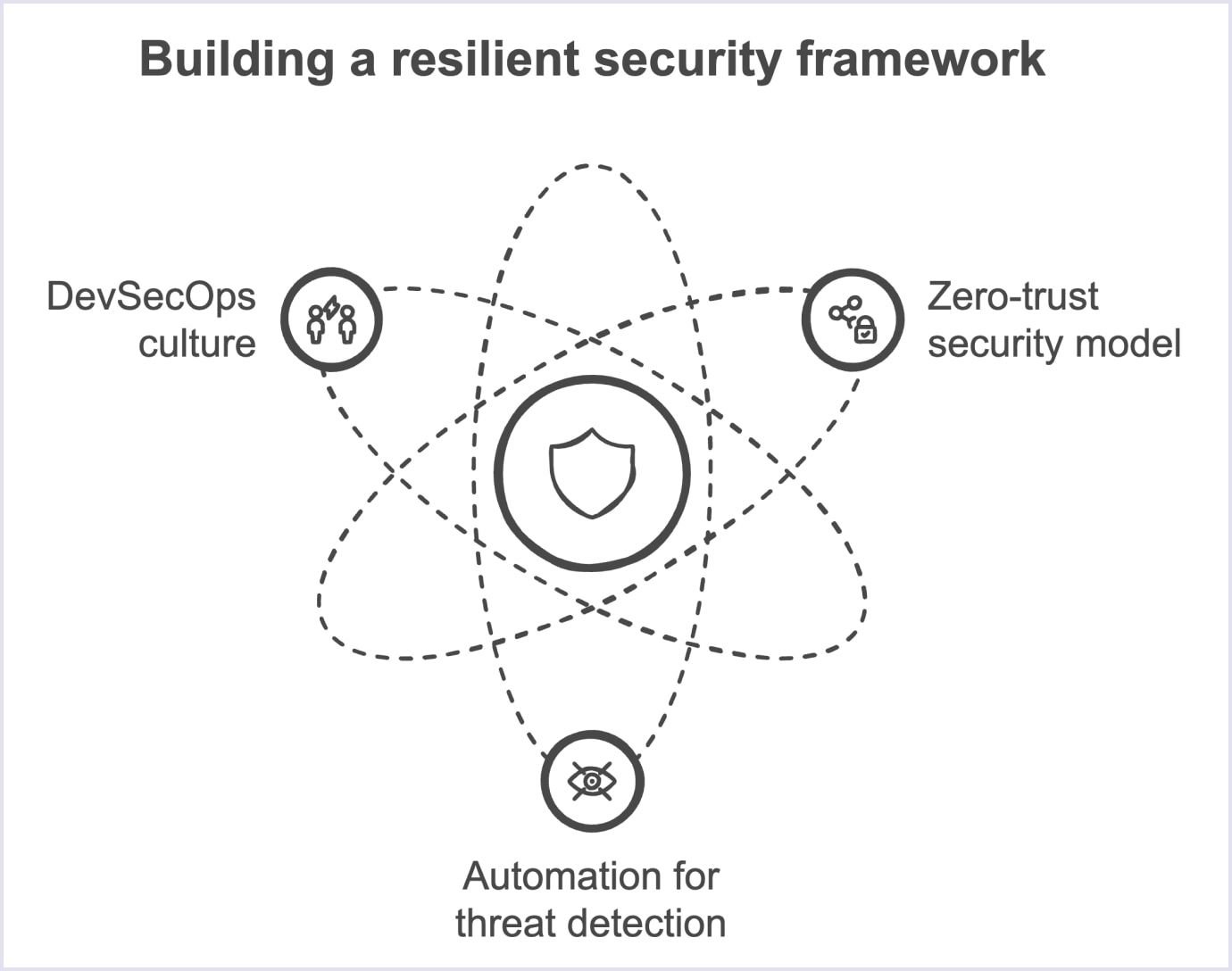
Adopt a zero-trust security model
The zero-trust security model assumes no user, device, or app is automatically trusted. Instead of using traditional defenses, it continuously verifies each entity trying to access resources.
This model enforces strict authentication, authorization, and encryption, ensuring every access request is validated, whether it’s from inside or outside the organization.
Now, let’s put it into a marketplace context. Zero-trust protects sensitive data because it requires multi-layered verification for all users and services.
For example, even internal requests between microservices are verified and encrypted, protecting the system from insider threats and compromised services. Zero-trust is especially useful in complex microservices, where isolating each service can reduce the impact of any breach.
Implement automation for threat detection
For any web product more complex than a landing page, automation is critical for modern security frameworks. They can perform a lot of tasks in the background, allowing you to save up costs on quality assurance services or save your employees time for more challenging tasks.
When implemented, automated systems can monitor network traffic, user activity, and API calls in real time, instantly identifying unusual patterns that could signal an attack.
Many automation tools are based on machine learning algorithms and AI, which also means that they learn as they work. These tools can trigger alerts or, in some cases, initiate preconfigured responses — like temporarily suspending suspicious accounts or isolating compromised services.
In the aftermath, automation not only speeds up threat detection but also enhances response times, reducing the potential damage of security incidents.
Read also: Boosting Business Security with Custom AI Solutions
Embrace a DevSecOps culture
Marketplace DevSecOps practices are an approach that rejects an outdated way of testing the product only after it was built. Instead, it introduces security measures into every step of the development process, adding a whole new layer of security.
Simply put, if you imagine a software development lifecycle as a timeline, DevSecOps shifts security “left,” meaning it’s addressed earlier in the process.
When it comes to marketplace development services, DevSecOps means involving security teams in design, coding, and deployment. This way, developers can catch and fix security issues early. Later, this approach often proves super useful as it reduces the cost and effort needed to address vulnerabilities in the later stages of the development.
Understanding security challenges in marketplace platforms
To protect users and maintain trust, your marketplace must address a variety of security challenges, from information protection to data privacy compliance regulations. Let’s list a few.
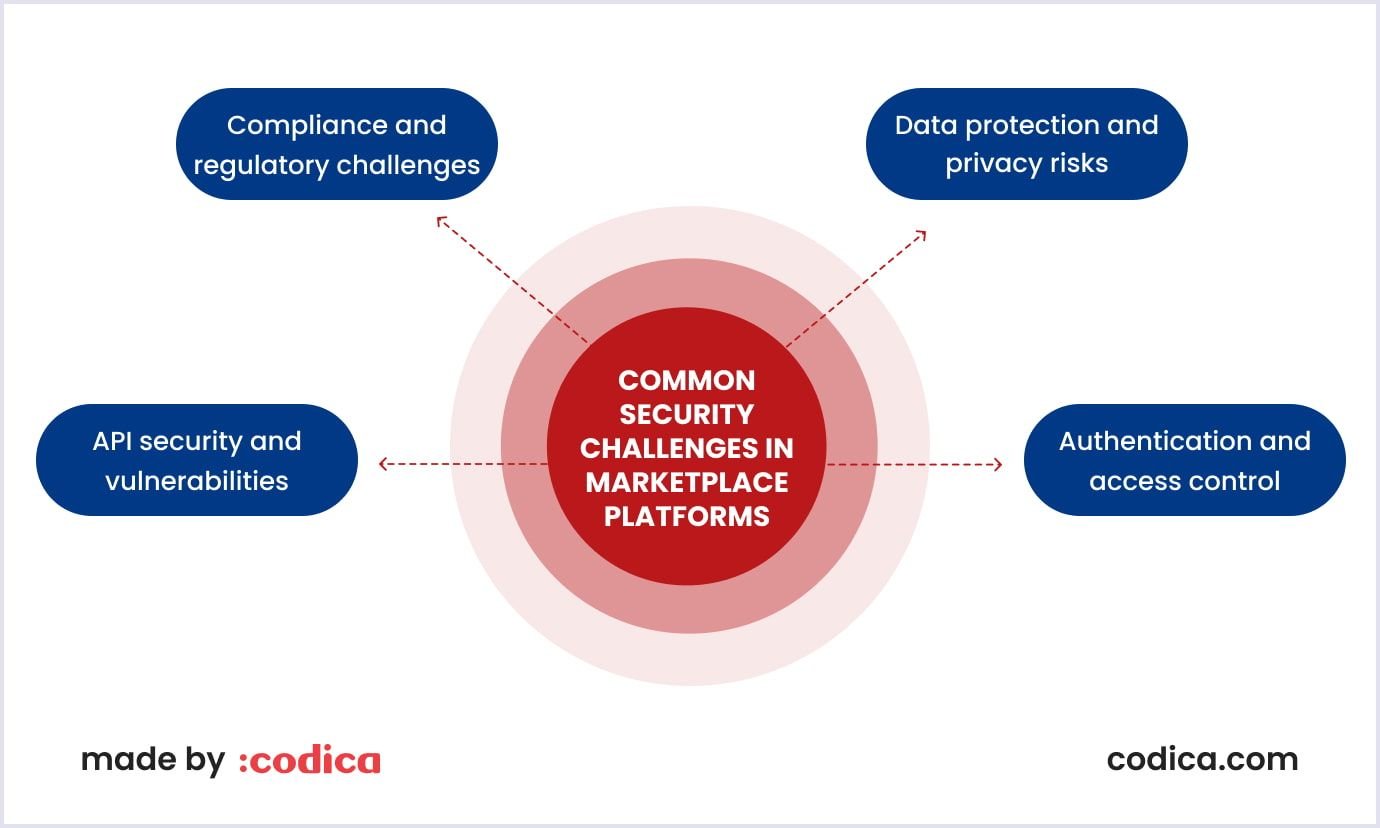
Data protection and privacy risks
Securing sensitive data is always a vital process for marketplaces. They store and process tons of important personal details and info like customer personal information, payment credentials, vendor-specific info, and much more.
Being confidential and valuable, this data is always at aim and has to be protected by any means. To protect it, your marketplace must provide enough security means, like encryption methods, secure data storage practices, and strict data access policies.
Besides these methods, you should also arrange manual work such as regular audits and vulnerability assessments.
Authentication and access control
Secure authentication and access control are essential to prevent criminals from tapping into confidential information without unauthorized access. Given the variety of users in a marketplace (customers, vendors, and administrators), implementing a multi-layered authentication system is vital. For example, it often includes strong password requirements, multi-factor authentication security, and role-based access control (RBAC).
RBAC, in particular, is crucial for marketplaces as it restricts access based on user roles, limiting exposure to sensitive information. For example, vendors should only have access to their own data, while customers should have control over their personal profiles.
API security and vulnerabilities
Application programming interfaces (APIs) are a fundamental part of any web product, including modern marketplaces. They make communication between front-end, back-end, and third-party services possible by simplifying and optimizing it.
However, APIs can also be an access point to launch an attack on your marketplace if not properly secured. In API vulnerability management, there are common issues like broken authentication, data exposure, and inadequate rate limiting, all of which can lead to unauthorized data access and manipulation.
Compliance and regulatory challenges
Because marketplaces work with sensitive data, it’s obvious they must comply with various data protection regulations to operate in particular countries and worldwide:
- In the EU, for instance, there’s a General Data Protection Regulation (GDPR) that imposes strict requirements on how businesses collect, store, and use personal data.
- In the US, the California Consumer Privacy Act (CCPA) does practically the same.
Achieving compliance involves implementing data protection practices that align with regulatory requirements. These always include data minimization, user consent mechanisms, and transparent data management policies.
Your marketplace, apart from having a clear privacy policy, must also let users exercise their data rights. Therefore, actions like account and data deletion, as well as access requests, must be clearly visible and accessible to your users.
Read also: How to Build a Marketplace Website in 16 Steps: The Ultimate Guide
Conclusion
Securing marketplaces can be tough at times, seeing the sheer amount of work that must be done. Fortunately, you are one step closer to seeing how much easier it is after you adopt MACH principles security.
Its modularity makes it easy to manage the efforts of QA specialists and developers. This, in turn, means a lot: you lift a ton of work off their shoulders, save precious funds and time, and ultimately receive a working marketplace faster.
MACH principles proved themselves irreplaceable for our marketplace development as well. At Codica, we build them from scratch, and thanks to this modularity, the marketplaces we build can scale, grow, and be developed in a reasonable time frame and within budget. Therefore, feel free to contact us if you’re seeking to create a highly secure marketplace.
