Modern days technology are hard to imagine without containers. We have a lot of different solutions outside of containers. For example, it is about serverless or the usual application-on-host model and many managed solutions like Heroku or Vercel. Despite that, containers, for many years, remain the most popular and widely used solution. And now, it is difficult to imagine that this will change in the next 5-10 years.
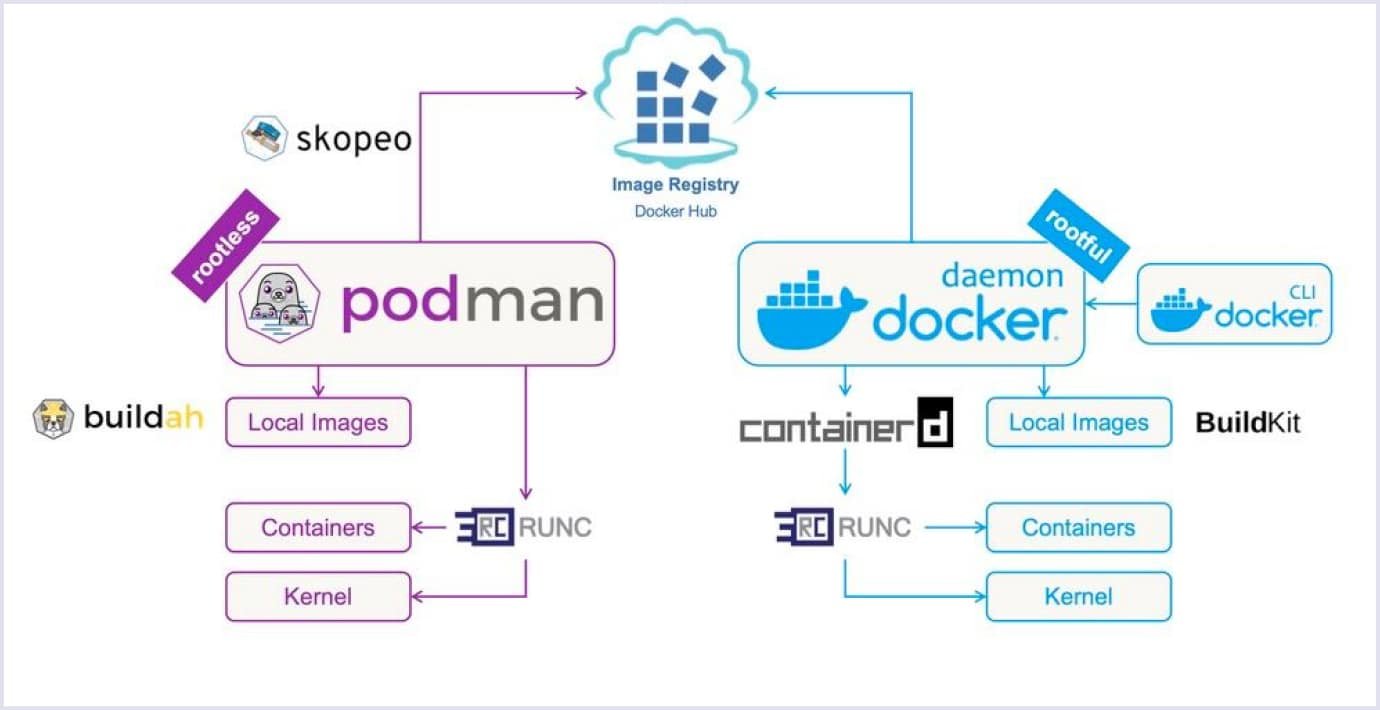
Nowadays, in the container world, we have two major players: famous Docker and less popular Podman from Red Hat. In fact, Docker is a platform for creating, shipping, and running apps in containers. Podman is a container management tool similar to Docker, allowing users to develop, run, and manage containers on Linux systems.
When talking about containers, it is crucial to understand that they are tied to operating systems. For example, container images and configurations are often customized for specific operating systems to ensure optimal performance and compatibility. But containers do rely on certain features and components of the host operating system to function.
In this article, our DevOps specialists have prepared detailed research of the main features and differences between the two container tools - Docker vs. Podman. Therefore, you will be able to analyze the core of these containers and apply them in your practice.
Let's briefly examine Podman vs. Docker containerization tools.
Containers background: brief overview
It all started at the end of 1960th when the first version of Unix was released. It was created by now-famous people who probably changed the IT world as no one did - Ken Thompson, Dennis Ritchie, Brian Kernighan, and others.
You likely think containers are a pretty new and modern technology. In practice, it mostly is, but its roots go deep into the 20th century.
Chroot
The precise definition is “run command or interactive shell with a special root directory." What does that mean? This tool creates a safe environment, separate from the rest of the system. Processes designed in the chrooted environment can not access files or resources outside of it.
Over the years, chroot spread across many other Unix and Unix-like operating systems. In BSD, chroot was first mentioned in version 2.9.1. As for Linux, in GitHub, you will not find anything older than 2005, “Linux-2.6.12-rc2.” Most likely, chroot was there since the first release of Linux as it was backward compatible with Minix.
Read also: AWS vs. Microsoft Azure vs. Google Cloud Services Comparison
BSD Jails
The next big step in the container's history of evolution is BSD (Berkeley Software Distribution) Jails. In general, BSD was an essential part of the operating system’s history and evolution.
According to the Apple documentation archive, “Darwin technology is based on BSD, Mach 3.0, and Apple technologies. Best of all, Darwin is Open Source technology, meaning developers have full access to the source code. In effect, OS X third-party developers can be part of the Darwin core system software development team.”
The image below illustrates the OS X architecture.
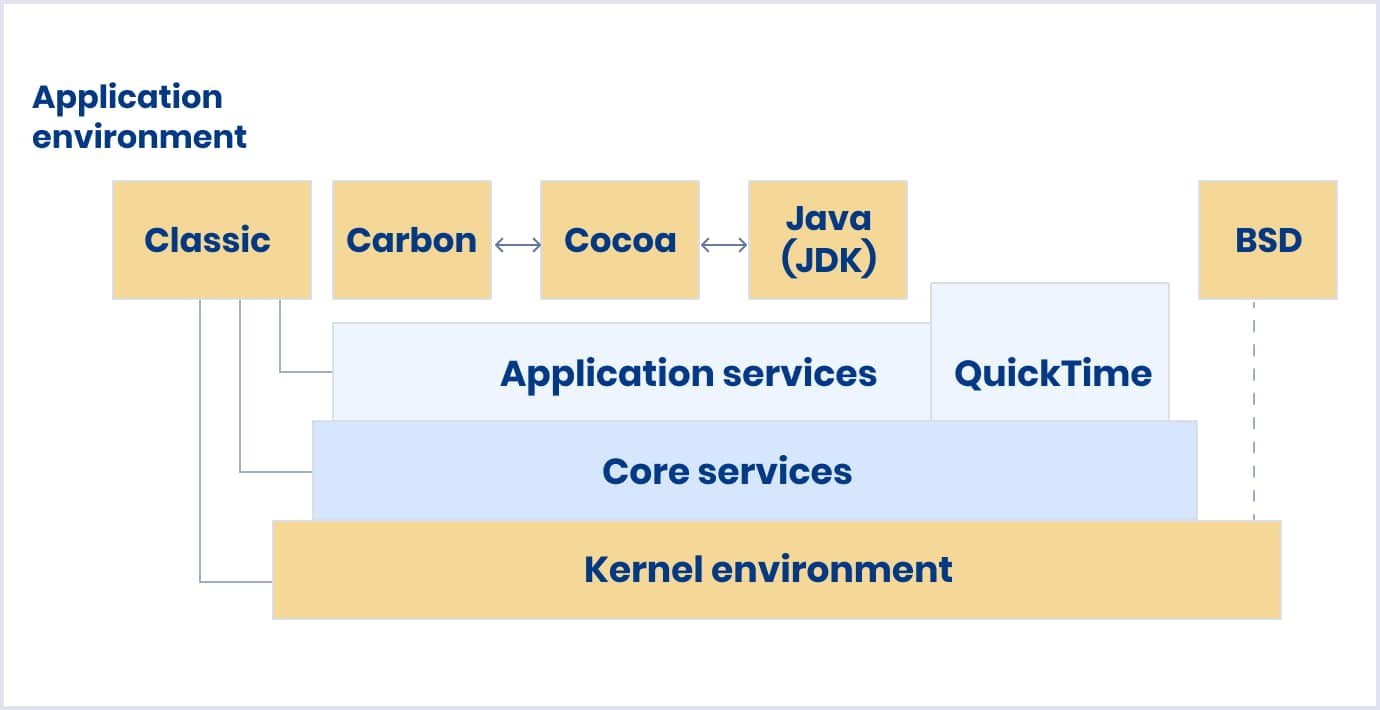
In a traditional chroot environment, processes are only limited to the part of the file system they can access. The rest of the system resources, system users, running processes, and the networking subsystem are shared by the chrooted processes and the processes of the host system.
Four elements characterize a Jail:
- A directory subtree;
- A hostname;
- An IP address;
- A command;
Jails have their own users and root accounts limited to the Jail environment. The root account of a Jail is not allowed to perform operations to the system outside of the associated Jail environment.
Namespaces
The history of namespaces started with the release of the Plan9 operating system. They were a big step forward when compared to previous isolation methods. In Linux, they appeared in 2002 with the release of kernel 2.4.19.
A namespace wraps a global system resource in an abstraction. This abstraction makes it appear to the processes within the namespace that they have their isolated instance of the global resource. Changes to the global resource are visible to other processes that are members of the namespace but are invisible to other processes.
Nowadays, we have several types of namespaces:
- PID (process identifier) namespace
The image below shows how a person knows the basic functionality of Linux and how everything works there. 
- UTS (Unix timesharing system) namespace
- Mountpoint namespace
- Network namespace
- ID’s namespace
- Inter-process communication namespace
- Control groups (or cgroups)
- Time namespace
Without namespaces, there are no containers. So, containers are built on top of their logic.
In this article, we will explore and compare the two most popular containerization tools. You will not dive into container orchestrators like Kubernetes because it is beyond the scope of this article.
Also, our experts recommend watching Liz Rice's talk, where she explains how everything works together.
Podman vs. Docker: key differences comparison table
Docker is a containerization technology that makes managing dependencies within a project at all levels (development and deployment) easy. The Docker engine is available for Linux, Windows, and macOS.
In general, Docker consists of two main building blocks.
- Docker CLI (command-line interface). Docker CLI is a Docker command line client for interacting with the Docker daemon. This is what you use when you run any Docker command.
- Docker daemon. The Docker daemon is a persistent background process that helps manage Docker images, containers, networks, and storage.
All container tools like Docker have an image-based deployment model. This model makes sharing an application or set of services easy across multiple environments.
In addition, Docker helps automate the deployment of applications in a container environment. With these various tools, users gain full access to the applications and can accelerate deployment, control versions, and assign them.
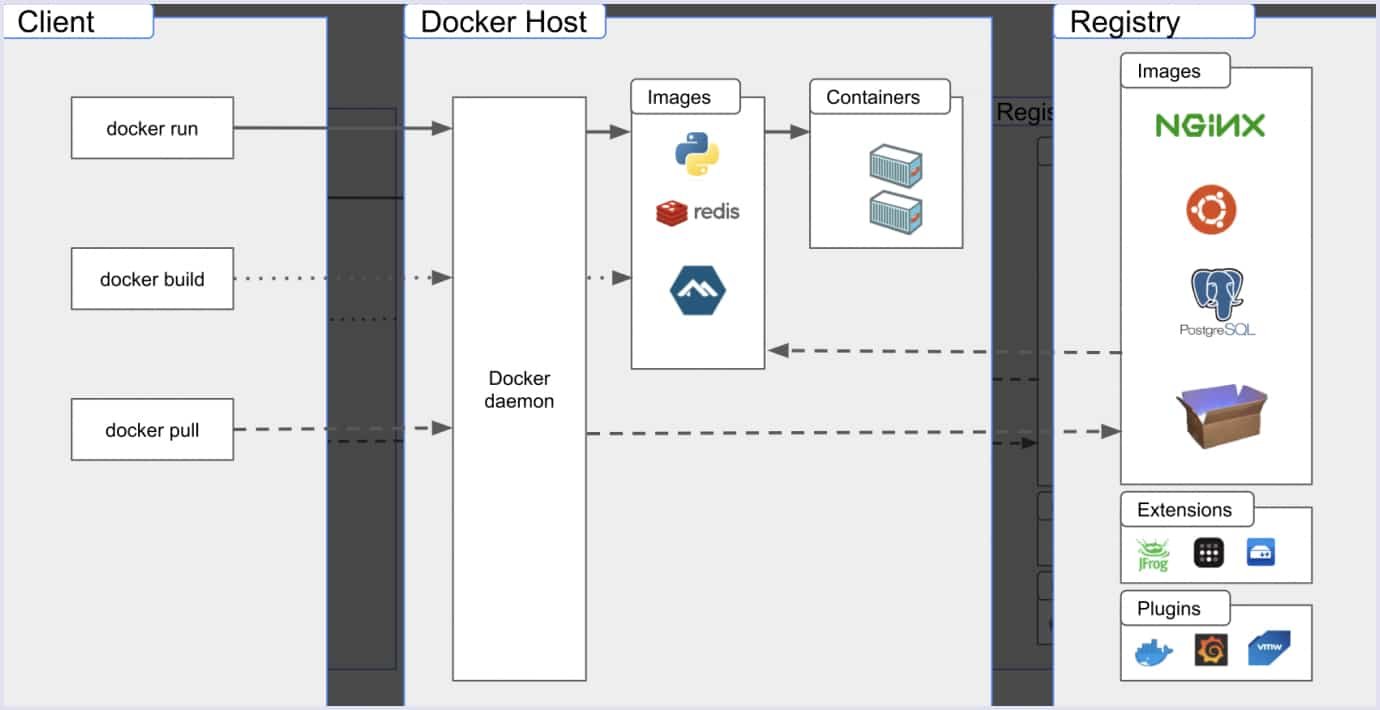
You can take a look at the Docker architecture below.
Podman creates, runs, and manages OCI containers and container images. It was developed by Red Hat and originally intended for enterprise Linux 8. Podman is used to manage containers and is the official opponent of Docker.
It manages the entire ecosystem of containers using the libpod library. Podman also supports modules for collaboratively working container groups and multiple image formats, including OCI and Docker.
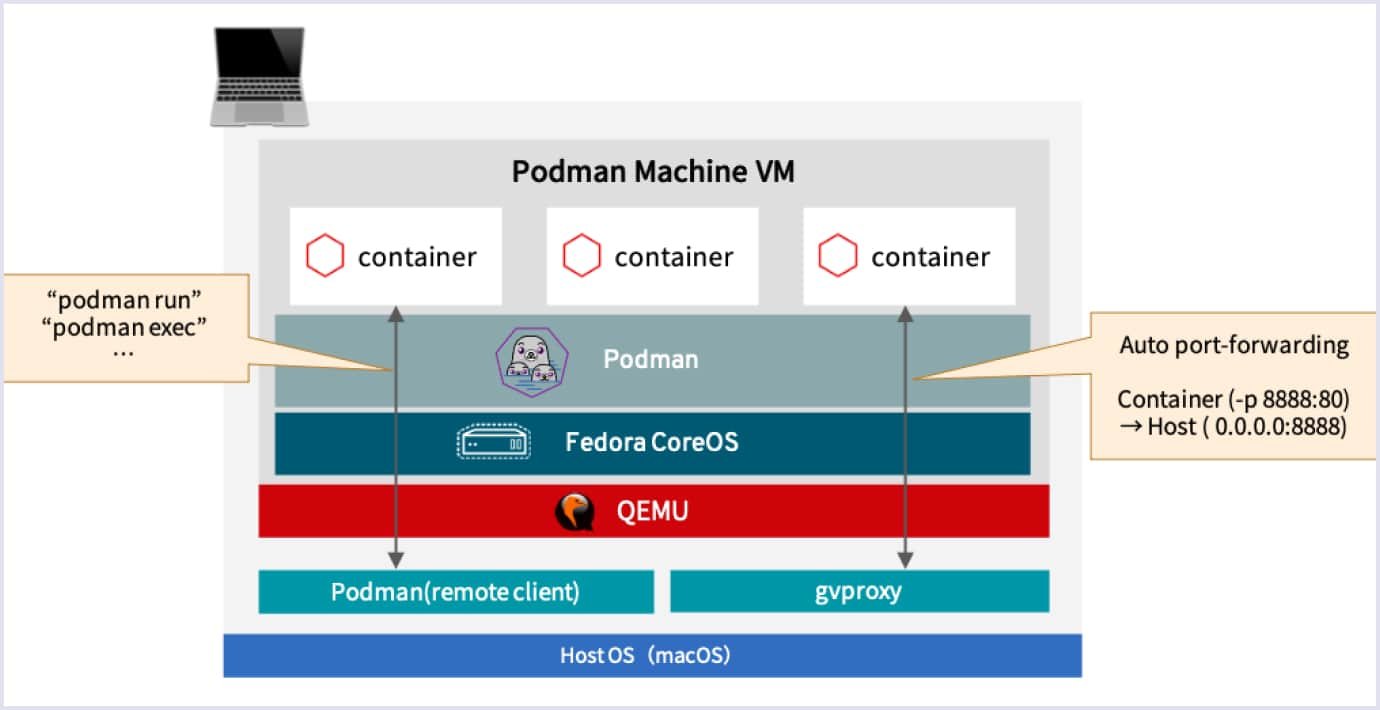
Below is the Podman architecture illustrated.
Podman can even serve as a precursor to Kubernetes (an open-source container orchestration system) in minimal and managed environments. It bridges the gap between unique individual instance management from the early years of container advertising and modern orchestration with Kubernetes. At its simplest, newly designed containers can be tested and refined in separate operations.
Now, let's move on to the comparison table of the Podman vs. Docker difference.
| Parameters | Docker | Podman |
| Daemon | Docker daemon | Daemonless |
| Root | Needs a root but also has a rootless solution | Rootless by default but can also use root |
| Build and builder | Has a bunch of builders, but BuildKit is the default since engine version 23 | Buildah |
| Monolithic | Monolithic | Non-monolithic |
| Support of docker compose | Yes | Yes |
| Supported platforms | Linux, Mac, Windows | Linux, Mac, Windows |
Thus, with the merge of BuildKit, Docker is now ahead of Podman in terms of features.
Podman vs. Docker: essential features
Podman and Docker are powerful containerization tools with their unique features. Your decision to choose one of them should align with your organization's goals, engineers’ familiarity with the tools, and the specific demands of your containerized applications.
Nowadays, the world of containerization continues to evolve, and both tools will likely remain essential players in this ever-expanding ecosystem. Let's explore in more detail the major features of Podman vs. Docker.
Performance
Regarding Podman vs. Docker performance, both solutions are fast. In specific cases, one is slower, and the other is faster. Here is a simple table where we compared execution\run\build time of some basic daily operations:
| Command | Docker | Podman |
| Build | 0m8.499s and 0m7.005s with BuildKit | 0m8.436s |
| Image list | 0m0.025s | 0m0.145s |
| Running a container | 0m0.481s | 0m0.245s |
Our specialists used a simple dockerfile with nginx and a few COPY and RUN statements to collect the necessary data. All tests were run on Ubuntu 22.04, the latest server AMI in AWS (Amazon Web Services). We tried those commands a few times, and they were executed a few times to ensure the data was accurate. As you may see, BuildKit, due to its parallelism, is powerful and way faster than old Docker and Podman’s build.
Also, CLI commands were way faster on Docker. Here, we can guess it's due to daemon architecture. Moreover, Podman makes way more system calls and communicates with systemd in our tests with strace.
Security
Discussing Podman vs. Docker security, you may have heard before that Podman is more secure. While it’s true, it’s not that simple. We will not dive deep, but it is crucial to focus on the most vital part - differences and security features.
Podman uses rootless containers, enabling non-privileged users (with limited system access) to use user namespaces to run containers. Next, Podman, by default, improves security. To cope with security demands, Docker has also added a rootless mode.
Also, it's easier to audit Podman. You can read more about the Podman model for running containers.
You may also like: DevOps Security: Challenges and Best Practices
Architecture
Those two tools have different architectures. Podman is daemonless, and Docker has a daemon in the background. By the way, mostly daemonless is a better approach.
Below, you can see a Podman vs. Docker architecture comparison chart.
And what is the problem with Docker? If there is a failure in the Docker daemon, then every child process has lost track.
- A single process could be a single point of failure.
- This process owned all the child processes (the running containers).
All Docker operations had to be conducted by a user (or users) with the same full root access. And because Podman doesn’t have a daemon, it has none of those issues.
Compatibility
Docker and Podman are both OCI compliant, so the transition will not be an issue from a runtime perspective. But Docker Desktop is a whole platform with many features like Docker Scout, subscriptions, and a Dev Environment with numerous things built-in. These features are not in the Podman desktop, at least now. This is a clear advantage of Docker.
Also, Podman does not support Docker Swarm, which isn’t in excellent condition nowadays. But Docker Swarm is still alive and can be helpful in small and easy-to-setup environments.

Podman vs. Docker: other crucial differences
There are a few differences between Podman's and Docker's way of working. Podman has an image auto-update feature, and it can be useful. For example, imagine a developer has released a security update for your image, and then Podman will auto-update this image.
In contrast, Docker typically requires manual intervention for image updates. With Docker, you'd need to monitor for updates manually, pull the updated image, and then redeploy your containers using the latest image.
Root privileges
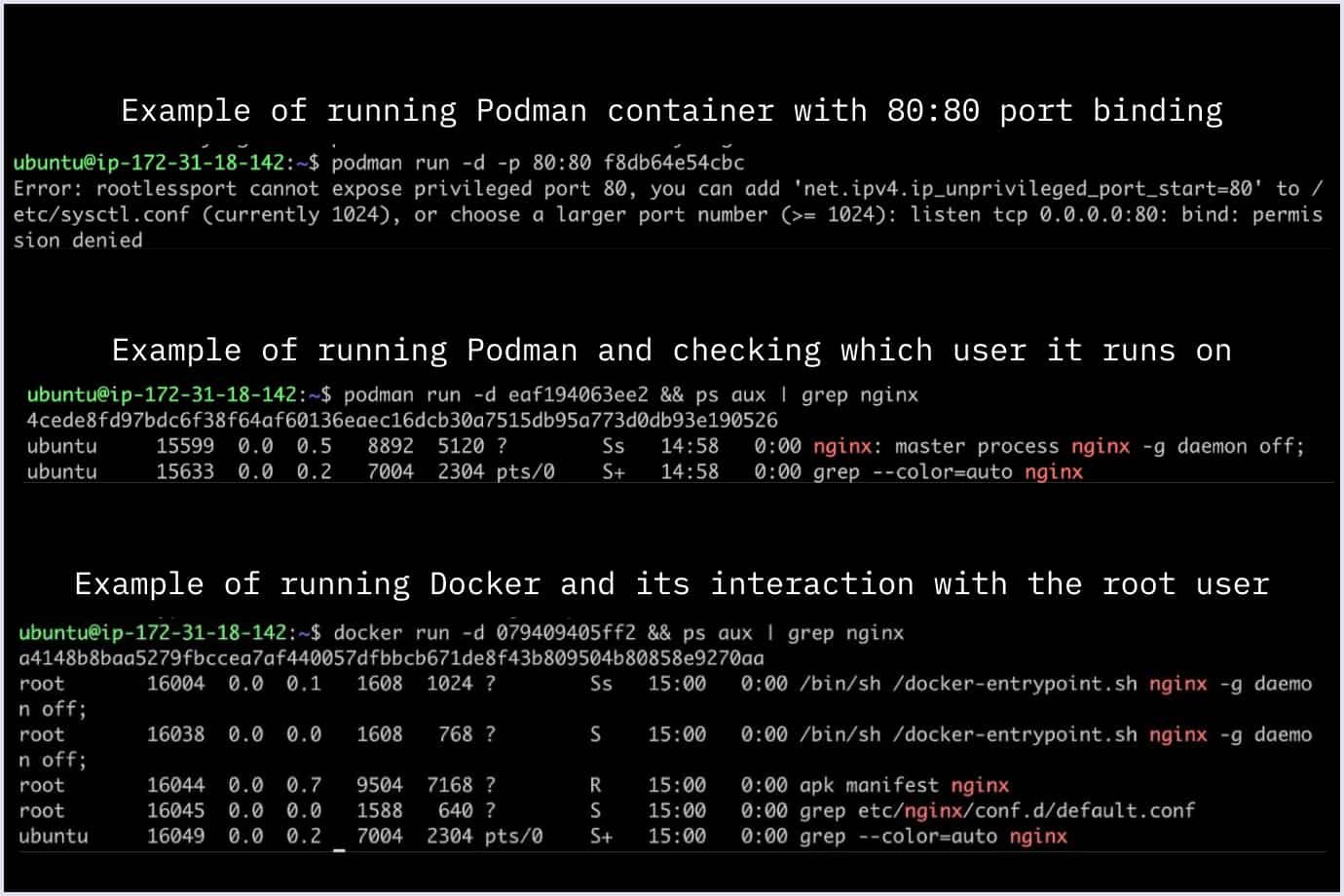
As mentioned before, Podman is rootless and doesn't need a root to run containers. There are some exceptions: you can't, for example, bind a port lower than 1024 because it requires Linux capability.
As you may see, Docker runs those containers as root users by default, and we can’t change it without using rootless.
Podman and Docker offer root and rootless modes for running containers. But Podman's architecture is more friendly to rootless containers, making them easier to set up and manage. While Docker's rootless mode requires a more complex configuration, Podman provides a smoother experience and more significant security benefits when running containers without root privileges.
Fork-exec model
Podman uses a traditional fork/exec model for the container, so the container process is an offspring of the Podman process. Docker uses a client/server model.
Specifically for this article, our specialists executed the Docker command. This command is the Docker client tool, and it communicates with the Docker daemon via a client/server operation. Then, the Docker daemon creates the container and handles communications of stdin/stdout back to the Docker client tool.
Image building
Nowadays, due to the merger of BuildKit, Docker has a clear advantage in terms of image-building time and features. BuildKit was introduced in 2017 as an experimental feature in Docker 17.05 and has since been integrated into the Docker engine as a core component.
Moreover, BuildKit is built on the OCI (Open Container Initiative) image specification and can create OCI-compliant images. Both builders create OCI-compliant images.
Our DevOps specialists suggest you read more about their comparison in the expert blog.
Docker Compose
In fact, Docker Compose is a tool that helps you define and share multi-container applications. With Compose, you can create a YAML file to describe the services. You can spin everything up or tear it down with a single command.
The significant advantage of using Compose is you can define your application stack in a file and keep it at the root of your project repository (it's now version-controlled). Also, you can easily enable someone else to contribute to your project. Someone would only need to clone your repository and start the app using Compose.
On the other hand, there are some advantages that Docker Compose brings to businesses:
- Speed up the development process;
- Organize sprints;
- Ease versioning of the product.
Both Docker and Podman support Docker Compose. By the way, for Podman, you can use podman-compose.
Read also: DevOps Tools You Should Know in 2023
Podman vs. Docker: pods and containers
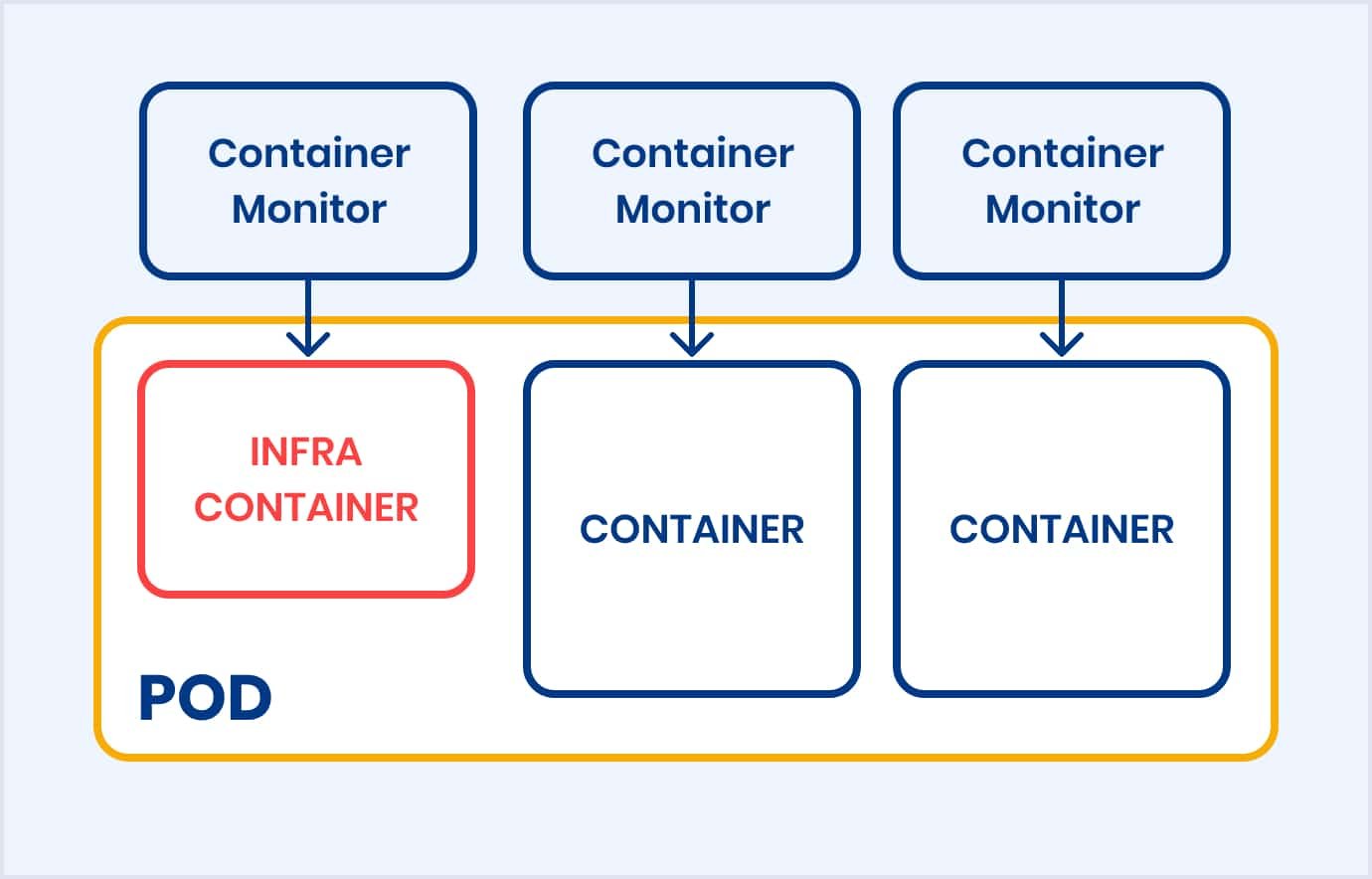
Podman provides features for managing groups of containers through pods. So, pods in the context of Podman refer to a grouping or collection of containers. Pods share specific network and storage namespaces, allowing them to work together as a single unit.
Each pod in Podman consists of an infra container and regular containers. The purpose of the infra container is to keep the pod alive and maintain the namespaces associated with the pod. Each container has a dedicated container monitor, a service that monitors container processes and logs exit codes if the containers die.
Below, you can see a graphical example of a typical Podman pod:
Suppose you have multiple containers that require, for example, a MariaDB (an open-source relational database system) container. But you would prefer not to bind that database to a routable network in your bridge or further. Using a pod, you could attach to the localhost address of the pod, and all containers in that pod will be able to connect to it because of the shared network namespace.
So, Podman can manage many containers in one command without using compose. While Docker has nothing like that, it only includes containers.
When talking about containerization, it is very often compared to virtual machines. But it is crucial to understand the main difference in the following image:
What does this image tell us:
- Containers are lightweight, isolated environments that package an application and its dependencies. They share the host OS kernel, making them efficient and portable.
- Virtual machines, on the other hand, emulate an entire operating system, including the kernel. They provide more robust isolation but consume more resources and take longer to start than containers.
Docker: pros & cons
In general, the Docker containerization platform offers numerous advantages, but it's not without its drawbacks. Let's explore the fundamental benefits and drawbacks of Docker.
Pros
- Docs: Docker has a lot of documentation about everything you may need.
- Community: Docker has a much bigger community and more contributors who are interested and contribute to Docker.
- Ecosystem: This containerization tool offers many different features, some of which Podman needs to improve. For example, it is about Scout and various integrations.
- Enterprise and business plans: Docker provides a lot of features for people who are willing to pay. For example, it is about integrations with popular repository providers like GitHub.
- Better builder performance: With BuildKit, Docker is way faster than Podman with Buildah.
Now, let's move on to the weaknesses of Docker.
Cons
- Worse rootless mode: In Podman, it is implemented way better and more accessible to use\setup.
- More threatening in terms of architecture: Docker daemon can bring a lot of issues. They can be related to resource intensity, attack surface, privileged access, and more.
In conclusion, Docker offers a powerful solution for containerization, enabling greater flexibility, scalability, and efficiency in software development and deployment. However, organizations should consider the learning curve and potential security and management challenges when adopting Docker in their workflows.
Podman: pros & cons
Certainly, Podman, an alternative containerization tool to Docker, has gained popularity for its unique approach to managing containers. It offers several advantages over Docker but also comes with its own set of disadvantages.
Let's go deep into the pivotal benefits and drawbacks of Podman.
Pros
- Better architecture: A fork-exec model is a better approach than a daemon.
- Excellent rootless mode: It works out of the box.
- Support of pods: Allows you to nicely and efficiently manage many containers together without having to compose.
Below, you can see certain disadvantages of Podman.
Cons
- Features: Podman has a much smaller community and, thus, has much less to offer regarding features.
- Slower builder: It feels significantly slower than Docker's BuildKit, which has been updated.
- Smaller community: The community is slower to respond. There are fewer GitHub contributors and less insightful information from the community.
- Documentation: Since the community is small, there are more occasional contributors and fewer regular updates.
Thus, Podman offers a compelling alternative to Docker, especially for users who prioritize security, rootless containers, and systemd integration. However, users should carefully weigh the advantages and disadvantages based on their specific use cases, familiarity with containerization tools, and the broader container ecosystem they must integrate with.

Podman vs. Docker: unveiling ideal use cases
In a nutshell, Podman and Docker are both containerization tools that serve similar purposes. However, they have some differences in their architecture and features, making them more suitable for specific use cases.
Let's explore when you might choose one over the other:
Use cases for Docker
If you have a large enterprise and need to keep everything in one place, Docker is a perfect fit. It is popular, has a lot of docs, a big community, and a lot of integrations and pricing plans for your company that will extend your usage.
You may also like: How to Choose Web Hosting for Your New Product
Use cases for Podman
Our specialists recommend using Podman if your company and you are security-oriented due to the better rootless mode. So, this rootless mode comes out of the box and works by default. Also, it is way easier to audit the mode's logs and statuses.
Podman vs. Docker: choosing your container champion
In our comparison research, we found that both solutions fit different scenarios and industries. These containerization tools can't perfectly replace each other, and they are developed by different companies and various sizes of communities. As a result of this analysis, Docker has a lot of exciting features, and so does Podman.
The choice between Podman vs. Docker ultimately comes down to your business needs, preferences, and environmental characteristics. Both containerization tools have their strengths and weaknesses, knowing which can help you make an informed decision.
If you are looking for reliable DevOps services and solutions, our specialists are ready to help with your business needs. Contact us and get high-quality software rapidly.
